What Are Vulnerability Management Tools?
Vulnerability management tools are software used to identify, assess, and manage security weaknesses in IT systems. These tools offer a systematic approach to inspect an organization’s network and digital assets for vulnerabilities that could be exploited by cyber threats.
The primary goal is to reduce risks associated with vulnerabilities before they can be leveraged by attackers. This is a crucial part of an organization’s cybersecurity posture, ensuring that proactive measures are taken against potential security breaches. These tools include various functionalities that address different aspects of vulnerability management.
From scanning systems for known vulnerabilities to providing guidance on remediation, each tool aids in maintaining system integrity. Their importance has grown with the increasing complexity of IT environments and the evolving nature of cybersecurity threats.
Table of Contents
ToggleKey Features of Vulnerability Management Tools
Vulnerability management tools typically include the following capabilities.
1. Asset Discovery and Inventory
The vulnerability management process begins with identifying all IT assets within an organization’s network. This includes hardware components, virtual entities, applications, and network components. Asset discovery ensures that no element is overlooked, allowing security teams to have a complete view of their technology environment.
This step is critical because unidentified assets could harbor vulnerabilities that an attacker might exploit. Once assets are discovered, maintaining an accurate inventory becomes essential. Regular updates to this inventory reflect changes, such as the addition of new devices or applications, ensuring the organization always has current data to work with.
2. Vulnerability Scanning
Vulnerability scanning involves systematically examining networks and systems for known vulnerabilities. These scans leverage databases of known threats, comparing them against an organization’s assets to identify weak points. This process can be scheduled at regular intervals or conducted on-demand, allowing for both periodic health checks and immediate assessments.
The effectiveness of vulnerability scanning depends on several factors, including the comprehensiveness of its threat database and the ability to execute non-intrusive scans. Comprehensive scans ensure that a wide range of vulnerabilities are detected, while non-intrusive processes minimize disruptions to operations.
3. Risk Assessment and Prioritization
Risk assessment and prioritization functions analyze identified vulnerabilities in terms of severity, potential impact, and exploitability to determine which pose the greatest threat. Not all vulnerabilities are equal; some might be critical with high potential impact, while others might have low significance. Prioritization helps allocate resources to fix vulnerabilities that matter.
By understanding the risk each vulnerability holds, vulnerability management tools can provide actionable insights. This allows organizations to prioritize patches and mitigations based on calculated risk rather than mere presence. It’s essential for organizations to align risk prioritization with their overall risk management strategy.
4. Remediation and Mitigation
Remediation involves applying fixes, such as patches or configuration changes, to eliminate the identified vulnerabilities. This process can be resource-intensive, depending on the complexity and number of vulnerabilities that need addressing. Vulnerability management tools often provide automation capabilities to simplify and speed up this process.
Mitigation focuses on minimizing potential damage if remediation cannot be immediately implemented. Strategies might include disabling vulnerable services, implementing access controls, or using intrusion prevention systems. While mitigation doesn’t eliminate vulnerabilities, it reduces the window of opportunity for exploitation.
5. Reporting and Compliance
Reporting and compliance are essential components of vulnerability management, aimed at providing visibility and accountability. Reporting features enable tracking the status of vulnerabilities and remediation efforts. By generating detailed reports, organizations can gain insights into their security posture over time.
Compliance requirements often dictate protocols for vulnerability management. Tools that offer compliance reporting can help organizations meet these standards by demonstrating adherence to regulatory requirements. This aspect is vital in industries with strict legal regulations around cybersecurity practices.
Types of Vulnerability Management Tools
Vulnerability management tools can be categorized into the following types.
Network-Based Scanners
Network-based scanners assess the security of an organization’s network infrastructure. They work by scanning network devices such as routers, switches, firewalls, and even endpoints for known security weaknesses. These tools detect vulnerabilities by simulating attacks and examining open ports, firewalls, and network services.
These scanners highlight vulnerabilities that specifically affect network protocols and configurations. They can provide insights into misconfigurations, outdated firmware, or default settings that could be exploited. By continuously monitoring network components, these tools ensure that any changes in the network configuration do not introduce new security gaps.
Host-Based Scanners
Host-based scanners focus on individual devices within an organization’s environment. They analyze operating systems, installed applications, and system configurations to identify vulnerabilities at the host level. Unlike network-based scanners that concentrate on infrastructure, host-based tools dig deeper into the security posture of individual machines.
This depth of inspection includes checking for missing patches, weak passwords, or insecure application settings. Key advantages of host-based scanners include their ability to provide a fine-grained view of vulnerabilities specific to each device. This granularity allows for targeted remediation, addressing vulnerabilities that pertain to application and operating system layers.
Application Scanners
Application scanners target vulnerabilities within software applications. They assess programs for security weaknesses that could be exploited to manipulate applications in unintended ways. These tools conduct tests such as static and dynamic analysis, evaluating source code, interfaces, and runtime behavior.
This thorough inspection aims to identify flaws like SQL injection, cross-site scripting, and insecure authentication mechanisms. Application scanners inform developers of coding errors or insecure practices that need addressing to fortify the security of the application layer.
Database Scanners
Database scanners assess and identify vulnerabilities within database management systems. These tools explore databases for weaknesses such as misconfigurations, unpatched systems, over-permissive access controls, and default passwords. Given the critical nature of data stored within databases, protecting them from unauthorized access or corruption is crucial for maintaining data integrity and confidentiality.
These scanners perform automated tests to evaluate the security state of databases, providing administrators with insights into potential security gaps. By continuously monitoring and hardening database environments, organizations can guard against data breaches and sensitive data exposure.
Notable Vulnerability Management Tools
1. Faddom
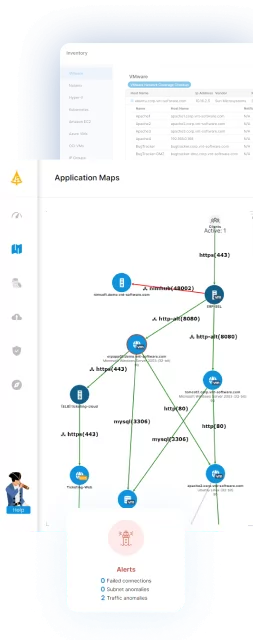
Faddom is an agentless application dependency mapping platform that provides real-time visibility across hybrid IT environments. It helps organizations strengthen vulnerability management by automatically mapping infrastructure, business applications, and dependencies, identifying risks like unpatched systems, CVEs, expired SSL certificates, and unauthorized software. With continuous discovery, risk prioritization, and powerful integrations, Faddom simplifies vulnerability management while improving security and resilience.
Key features include:
- Agentless, real-time discovery: Automatically maps on-premises and cloud infrastructure without agents or credentials; deploys in under 60 minutes.
- Vulnerability detection: Identifies CVEs, monitors SSL certificate status, and detects abnormal traffic patterns.
- Advanced risk prioritization: Highlights critical risks by analyzing lateral movement, external traffic, and user access.
- Software change and EOL/EOS monitoring: Detects unauthorized software changes and end-of-support or end-of-life software.
- Integration-friendly: Connects with ServiceNow, CMDBs, ITSM/ITAM platforms, and SIEM tools via native APIs.
- Operational resilience: Supports incident management, root cause analysis, change planning, cloud migration, and compliance reporting (including DORA and NIS2).
2. Rapid7 InsightVM
Rapid7 InsightVM is a vulnerability management solution for dynamic IT environments. It provides continuous visibility into an organization’s attack surface through flexible scanning and asset discovery. Supported by AI and enriched threat intelligence, it helps security teams prioritize vulnerabilities based on risk as well as severity.
Key features include:
- Flexible scanning options: Supports both agent-based and agentless scanning to ensure broader coverage.
- Dynamic asset discovery: Continuously identifies new and changing assets across environments.
- Unified endpoint agent: Provides data collection and risk visibility across endpoints.
- AI-driven risk prioritization: Uses the Active Risk scoring model to factor in exploitability, attacker behavior, and business impact.
- Live dashboards and reporting: Offers customizable dashboards for monitoring and decision-making.
Source: Rapid7
3. Tenable Nessus
Tenable Nessus is a vulnerability assessment solution to help organizations identify, prioritize, and address security flaws across diverse IT environments. Built with practitioner experience in mind, Nessus provides vulnerability scanning, configuration auditing, and compliance checks that can be deployed across a variety of platforms.
Key features include:
- Vulnerability assessments: Perform scans across operating systems, devices, applications, and cloud infrastructure.
- Scoring and prioritization: Supports CVSS v4, EPSS, and Tenable’s VPR to rank vulnerabilities based on real-world risk factors.
- Configuration and compliance audits: Conducts assessments to verify adherence to security policies and regulatory standards.
- Platform support: Deploys on various systems including cloud environments and devices like Raspberry Pi.
- Web and external attack surface scans: Scans web applications (up to 5 FQDNs by default) and external-facing assets for exposure risks.
Source: Tenable
4. CrowdStrike Falcon Spotlight
CrowdStrike Falcon Spotlight is a scanless vulnerability management solution built into the CrowdStrike Falcon platform. It delivers continuous visibility into vulnerabilities without the overhead of traditional scanning infrastructure..
Key features include:
- Scanless vulnerability assessment: Delivers continuous monitoring without the delays and disruptions of legacy scans.
- Single lightweight agent: Uses the existing Falcon agent—no additional deployment or infrastructure required.
- Real-time visibility: Instantly detects new vulnerabilities, typically within 8 hours of CVE detection rule updates.
- Cloud-native architecture: Ensures fast deployment and minimizes performance impact on endpoints.
- AI-driven prioritization: Leverages ExPRT.AI to improve prioritization efficiency, focusing attention on the most critical risks.
Source: CrowdStrike
5. Qualys VMDR
Qualys VMDR (Vulnerability Management, Detection, and Response) is a risk-based vulnerability management solution built on the Qualys Enterprise TruRisk™ platform. It combines asset discovery, vulnerability detection, risk-based prioritization, and remediation into a workflow-driven solution.
Key features include:
- Unified asset and vulnerability management: Helps discover and track all assets, including cloud, containers, mobile, and on-premises.
- TruRisk™ scoring and prioritization: Leverage multiple sources of threat intelligence to assign contextual risk scores.
- Continuous monitoring: Detects new risks and zero-day vulnerabilities faster than traditional scanning tools with cloud agents and passive sensors.
- Automated remediation workflows: Allows users to deploy patches directly or generate tickets in ITSM tools to close the remediation loop and reduce mean time to remediation.
- Native patching and mitigation: Applies fixes or mitigations without the need for external tools or manual coordination.
Source: Qualys
6. Cisco Vulnerability Management
Cisco Vulnerability Management (formerly Kenna.VM) is a risk-based vulnerability management solution that helps organizations prioritize and remediate vulnerabilities using a combination of analytics and threat intelligence.
Key features include:
- Risk-based prioritization: Uses data science and threat intelligence to identify vulnerabilities that most significantly reduce risk when remediated.
- Threat forecasting: Predicts vulnerability weaponization, allowing remediation before exploits occur.
- Contextual threat intelligence: Aggregates multiple threat intelligence feeds to provide a view of the evolving threat landscape.
- Unified risk view: Centralizes asset and vulnerability data to provide a single, verified source of truth across teams.
- Intuitive risk scoring: Generates simplified risk scores and visual reports, making it easier to communicate risk across technical and non-technical stakeholders.
Source: Cisco
7. ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus is a cross-platform vulnerability management and compliance solution that offers visibility, assessment, and remediation. It enables organizations to detect and mitigate operating system and third-party software vulnerabilities, security misconfigurations, and high-risk applications in local and remote environments.
Key features include:
- Vulnerability assessment: Detects vulnerabilities across operating systems, third-party software, and zero-day threats. Prioritization is based on severity, exploitability, asset impact, and fix availability.
- Integrated patch management: Automates patch download, testing, and deployment for Windows, macOS*, Linux, and third-party applications.
- Security configuration management: Identifies and remediates system misconfigurations related to credentials, privileges, firewalls, and access controls based on CIS and STIG benchmarks.
- Compliance auditing: Supports over 75 CIS benchmarks and provides compliance checks with remediation guidance to help meet audit requirements.
- Web server hardening: Detects and addresses security flaws in internet-facing systems, including HTTP misconfigurations, expired certificates, and potential cross-site scripting risks.
Source: ManageEngine
8. Intruder
Intruder is an attack surface and vulnerability management platform to help organizations stay ahead of emerging threats. It continuously monitors the environment for exposed assets and vulnerabilities, kicking off scans automatically when changes are detected.
Key features include:
- Attack surface discovery: Automatically uncovers unknown assets such as subdomains, APIs, login portals, and related domains by connecting to cloud providers like AWS, Azure, GCP, and Cloudflare.
- Continuous vulnerability scanning: Triggers scans when new services are exposed and checks for the latest threats using threat intelligence feeds.
- Exposure management: Detects over 1,000 types of attack surface issues—including exposed databases and admin panels—that traditional scanners often miss.
- Prioritization: Enhances CVSS scoring with data from sources like CISA’s Known Exploited Vulnerabilities list and EPSS predictions to focus on the most exploitable and impactful issues.
- Private bug bounty program: Provides access to a team of ethical hackers who identify high-impact vulnerabilities beyond what automated scanners can detect, such as subdomain takeovers and credential leaks.
Source: Intruder
9. OpenVAS
OpenVAS (Open Vulnerability Assessment System), developed and maintained by Greenbone, is an open-source vulnerability scanner that is part of the Greenbone Community Edition. Originally forked from Nessus in response to its move away from open-source, OpenVAS has evolved from a basic scanning engine into a component of Greenbone Vulnerability Management (GVM).
Key features include:
- Full-featured vulnerability scanning: Supports a range of protocols and testing methods, including both high-level internet protocols and low-level industrial protocols.
- Authenticated and unauthenticated testing: Performs scans with or without credentials to identify vulnerabilities from internal and external perspectives.
- Daily updated vulnerability feed: Relies on a feed of vulnerability tests provided by Greenbone and partner contributors.
- Large-scale scan support: Offers performance tuning and scheduling capabilities for efficient handling of scan operations across large environments.
- Custom test development: Includes an internal scripting language, enabling users to write and deploy custom vulnerability tests.
Source: Greenbone
10. ThreatMapper
ThreatMapper is an open-source, cloud-native application protection platform (CNAPP) that provides visibility across infrastructure. It scans for vulnerabilities, misconfigurations, malware, and exposed secrets across cloud, container, and serverless environments. It is freely available under the Apache 2.0 license.
Key features include:
- Full-stack vulnerability scanning: Detects vulnerabilities, exposed secrets, misconfigurations, and malware across workloads, including VMs, containers, Kubernetes, and serverless.
- ThreatGraph-based risk prioritization: Correlates findings with exploitability and context using the ThreatGraph engine to highlight the most critical threats.
- Topology mapping: Provides a visual map of cloud infrastructure, uncovering hidden services and internal attack surfaces for better risk awareness.
- eBPF-driven observability: Uses lightweight eBPF sensors for network and application insight without performance degradation.
- Continuous compliance monitoring: Helps maintain alignment with frameworks like CIS, PCI, HIPAA, GDPR, NIST, and SOC 2 by identifying gaps and offering actionable remediation guidance.
Source: Deepfence
Conclusion
Vulnerability management is no longer just about scanning and patching; it’s about achieving continuous, comprehensive visibility across the entire IT landscape. As environments become increasingly hybrid and complex, tools that combine application dependency mapping, real-time risk detection, and intelligent prioritization offer a transformative advantage.
By understanding how assets, business applications, and users interact, organizations can proactively identify vulnerabilities, reduce attack surfaces, and minimize risk; all while ensuring operational resilience and regulatory compliance. This application-centric, holistic approach is fast becoming the gold standard in modern cybersecurity programs.