Many organizations are in the dark when it comes to their network traffic. However, if IT can’t track what’s going on in their networks, they’re likely to run into a number of problems:
- Performance. What’s using network bandwidth? This information helps identify and fix bottlenecks.
- Security. What’s coming in and out of the network? This information helps identify and stop security threats.
- Compliance. What kind of traffic is on your network? This information helps comply with industry regulations.
NetFlow and sFlow are two network traffic monitoring technologies that can help solve these problems. That said, both NetFlow and sFlow have distinct advantages and drawbacks, so it’s important to choose the one best suited to specific organizational needs. In addition, embarking on any major IT transformation project, such as rolling out network traffic monitoring, can be a complicated task that is fraught with challenges.
Table of Contents
ToggleIn this post, we’ll compare NetFlow and sFlow to help organizations decide which is most appropriate for their needs, then offer some tips and best practices to ensure a smooth, seamless rollout.
Two Leading Network Traffic Monitoring Technologies: NetFlow and sFlow
Traffic monitoring involves collecting and analyzing traffic flow data. This information helps IT and security teams identify and troubleshoot performance issues, security threats, and potential compliance problems. Two leading traffic monitoring solutions are NetFlow and sFlow.
What Is NetFlow?
Developed by Cisco Systems in the mid-1990s, NetFlow is a network monitoring protocol that gathers and relays traffic data. It works by summarizing traffic data from each flow and sending it to a central collector. NetFlow gathers data on every packet entering or leaving a network device like a router or switch. The information NetFlow collects includes source and destination IP addresses, port numbers, protocol type, and packet size. Once sent to a NetFlow collector, the data is aggregated and analyzed to provide insights into network traffic patterns.
Figure 1: How traffic data flows using the NetFlow protocol (Source: Amp via Wikimedia)
What Is sFlow?
sFlow was developed by the InMon Corporation in the early 2000s to address concerns about overhead and resource usage associated with NetFlow. It aims to provide similar network traffic visibility while minimizing the burden on the monitoring device.
sFlow captures a subset of packets that pass through a network interface, typically one in every N packets. Packet information is then encapsulated into sFlow datagrams and sent to an sFlow collector, where it is analyzed to provide insights into network traffic patterns.
NetFlow and sFlow: Similarities
NetFlow and sFlow have a few things in common. Both can be implemented on a variety of network devices, including routers, switches, and firewalls. Both offer flexibility in terms of data collection and analysis options. And both can be very helpful in network management and performance optimization.
However, without adequate preparation, implementing any network traffic monitoring technology can be a complicated task—whether NetFlow, sFlow, or another solution. To prepare, organizations should perform application dependency mapping (ADM) for a fuller picture of how applications use the network environment and interact within it.
NetFlow vs. sFlow: Key Differences
Despite some commonalities, there are also marked differences between these two technologies, as seen in the following table:
| Feature | NetFlow | sFlow |
| Sampling Method | Collects data on every packet that enters or exits an interface; sends data to a centralized collector (centralized) | Collects data on a subset of packets that pass through a network interface; sends data to designated analyzers or tools (distributed) |
| Supported Devices | Proprietary protocol, supported by most Cisco devices | Open-source protocol, supported by a broader range of network devices |
| Supported Traffic | Supports IP traffic only, such as web, email, and file transfers | Network layer independent, meaning it can sample local, inter-network, inter-application, and other types of traffic |
| Performance | Can be resource-intensive, especially on high-traffic networks | Uses sampling, which is less resource-intensive |
| Scalability | May not scale well in large networks, slowing down network traffic or leading to data loss (may require hardware acceleration or other modification to scale) | May scale better than NetFlow since it is less resource-intensive, with lower impact on network traffic |
| Distributed Networks | NetFlow sends all traffic data to a single collector, which can become overwhelmed with a large volume of data from a distributed network | Designed around a distributed model |
| Accuracy and Granularity | Provides highly accurate and granular data | Provides less accurate and granular data, but still sufficient for most purposes |
| Cost | Requires a license from Cisco; price scales with network size | Free (open-source) |
NetFlow vs. sFlow: How to Choose?
There are a number of factors in the network environment, including bandwidth, CPU, device type, and network configuration that influence the choice of network traffic monitoring technology. Due to these variables, the choice is complex, and no one solution is right for every organization.
Organizations might want to choose NetFlow if…
- They need the most accurate and granular data possible.
- The network supports only IP-based traffic.
- They need 100% accuracy in monitoring network traffic.
Organizations might want to choose sFlow if…
- The network supports a multiprotocol environment.
- The organization needs to collect data from a large number of devices from multiple vendors.
- Performance constraints such as bandwidth and CPU might be an issue.
Another major factor to consider is cost: sFlow is free, while NetFlow requires a license from Cisco.
It’s also possible to create a hybrid configuration, combining NetFlow and sFlow on different devices to meet network traffic monitoring needs. For example, an organization might use NetFlow for critical applications and high-value data while also using sFlow for less critical applications and bulk data collection. Today’s newest flow monitoring tools often support both technologies, so organizations can leverage the best technology for each use case.
Best Practices for Embracing Modern Network Traffic Monitoring
Whichever network traffic monitoring protocol is right for an organization, the following best practices will ensure that the transition goes as smoothly as possible:
Define Clear Goals and Objectives
It is essential to understand the purpose of implementing network traffic monitoring technology; the technology selected and its configuration will depend on the specific performance, troubleshooting, or security issues an organization needs to address.
Get the Big Picture
Application dependency mapping (ADM) is a crucial first step before any transformational IT project of this type. It will provide a complete picture of how applications interact and use the network, along with bottlenecks and problems with the existing configuration. This enables educated decision-making every step of the way.
Choose the Right Technology
Technology and tooling decisions should be made in light of the organization’s goals and the insights gained from ADM, along with the scalability, accuracy, and ease of configuration of different options. Of course, budget must also be taken into consideration.
Start with a Pilot
Partial implementation allows organizations to gauge the performance and effectiveness of a traffic monitoring solution before expanding to the entire network. Performing ADM before implementing a network traffic monitoring technology can help identify ideal groups of devices (for instance, those not running business-critical apps or services) for a pilot run.
Monitor and Analyze Data
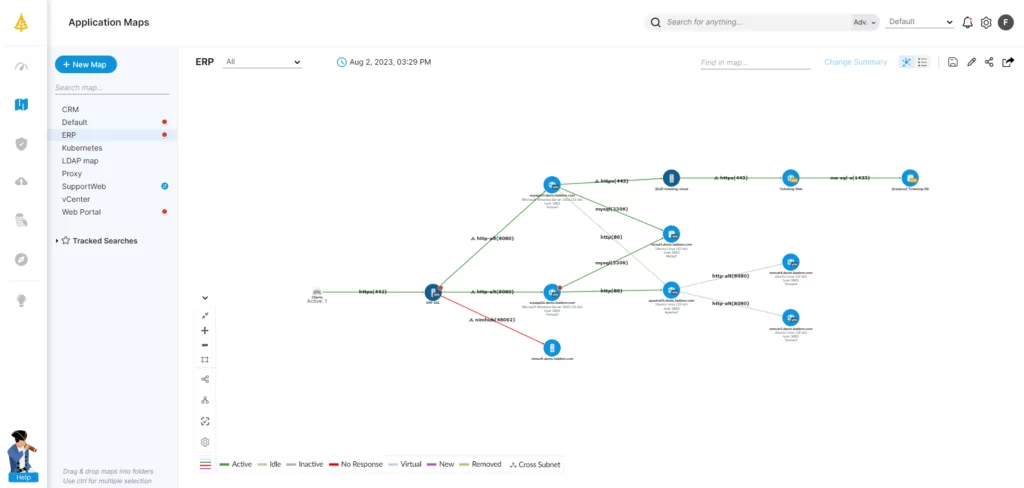
After collecting initial baseline traffic data, all traffic data should be regularly reviewed and analyzed to flag significant changes or potential problems. There are many tools out there to help achieve full visibility.
Application dependency mapping can also help optimize traffic flow at later stages by aiding IT teams in understanding how applications function within the network environment. For example, after any type of IT transformation project, ADM can help you find out which applications are generating the most traffic, which are experiencing slowdowns and bottlenecks due to network issues, and identify problems with dependencies.
For organizations that are ready to take the leap, Faddom is a key partner. Before rolling out any network traffic monitoring protocol, unveil the intricacies of your network’s topology and traffic patterns in under 60 minutes with Faddom’s real-time dynamic dependency mapping. Faddom helps organizations effectively plan and implement successful network monitoring using either NetFlow or sFlow, empowering proactive issue resolution and optimal network performance.
To get started with a free trial, just fill out the form on this page!