Every business in every sector bent on competing in the digital age will have to consider a legacy system migration as they grow larger—and their systems grow older. Business leaders often make what they consider to be practical IT requests to meet market, operations, customer, and competitive demands. However, it is the IT leaders and teams that must make IT sense out of those requests where legacy systems are affected.
Over 1,400 IT professionals surveyed for a recent Rackspace/AWS report said they are using an average of 22 legacy systems or applications that are taking up nearly 30% of their organization’s IT budget. They are not alone. Countless other IT professionals and stakeholders clearly see the business, operations, and customer costs of legacy systems.
Table of Contents
ToggleHowever, making business and IT sense of legacy migration is still a complex challenge that requires organizations to have a deep understanding of those systems and an ability to match their strategy with desired outcomes. This starts with understanding exactly what a legacy system is and what a legacy system migration entails.
What is Legacy System Migration?
A legacy system migration is about replacing an outdated computer system or application, such as monolithic applications on a mainframe, older databases, and/or the data and workloads on such databases, with modern systems. A system can become a legacy system due to various factors, such as an outdated framework, architecture, or programming language.
These aspects can also reveal a lack of internal IT knowledge about the system because of poor documentation over time, constant changes that accrue technical debt (which we will discuss later), and IT staff who lack the legacy language and programming skills used to build the original system.
These older systems lack scalability and the ability to integrate with newer technologies to meet changing operational, market, and customer demands. They also often pose risks in terms of regulatory compliance or attack vulnerabilities, not to mention they lack the ability to back up systems and their data for business continuity and disaster recovery. All of these issues can lead to costly downtime.
Although legacy system migration has some challenges this blog will discuss later, it is the benefits that drive most businesses to make the move.
Benefits of Migrating Legacy Systems
Migrating legacy systems offers a myriad of advantages, yet it’s crucial for businesses to distinguish between legacy system migration and modernization.
While migration replaces old systems entirely, modernization simply upgrades the existing legacy system. Still, organizations face a difficult choice between keeping, migrating, or modernizing their applications and systems. When looking at 23 enterprise applications used by 2,875 surveyed respondents, on average, 51% expect to keep their current applications while 46% plan to replace them in the next three years, according to IDC’s 2023 SaaSPath Survey.
The benefits of migration are a powerful draw that can include enhanced compliance with up-to-date regulations, heightened security, and potential long-term cost savings because of lower maintenance. Transitioning to modern systems can also result in increased efficiency and an enhanced user experience across all devices. Migrating from monolithic applications and systems to cloud-native applications and SaaS additionally enables ongoing scalability that traditional legacy systems cannot provide.
Challenges in Legacy System Migration
Despite the above and other benefits brought by legacy system migration, the process itself has some inherent challenges.
Technical Debt
As systems change over time, they often accrue technical debt. The reason for this is that it is often more expedient and cost-effective in the short term to integrate quick fixes into an outdated system than to completely restructure it. This is true for everything from mainframes and applications to networks and data centers.
Compatibility Issues
As a business updates its systems that interact with legacy systems, interoperability can be a problem, and compatibility issues that arise can accelerate the accrual of technical debt. A single monolithic application, workload, or database can lead to issues with network updates or the use of cloud platforms where other interacting applications and workloads live.
Resource Limitations
The migration process can reveal a tangle of dependencies that must be mapped and understood to avoid downtime during and after the migration process. This can be a multifaceted problem, ranging from choosing, acquiring, and learning the right tools to the costs of those solutions, platforms, and IT time. Then there is the resource challenge of having the right personnel with the skills and time to devote to the process.
Downtime and Data Security
Legacy system migration can result in planned and unplanned downtime that must be managed and minimized through migration stages, as opposed to a rip-and-replace strategy that can affect operational speed.
The data migration process can also be highly complex since clean and accurate data are paramount. Legacy system migration can pose many security risks to an organization’s data, ranging from the data transfer process to security flaws in its data access control and architecture.
Despite these challenges, every business can improve its chances for a successful legacy system migration by following some basic steps.
Legacy System Migration: Step by Step
Legacy system migration will vary from system to system and business to business, but there are many steps that are fundamental to the process.
Assembling the Team
The first phase consists of getting together the migration team, which should include critical IT team members along with primary system users across departments. It’s imperative that each member understands their role and the prescribed goals of the project.
Initial Assessment and Mapping
The next step is the assessment phase where applications, workloads, networks, and other related IT systems must be evaluated to determine the goals of the migration process. This reveals aspects of the system that are not working properly, their dependencies, and where IT teams can make improvements. The process will also enable the identification of any compatibility problems that may arise.
Define the Migration Objectives and Scope
Once the IT team has uncovered any legacy system issues, they can move on to making decisions about the migration project’s scope and objectives. This can vary from a data center migration to cloud migration and repatriation. The objectives may be operational efficiency, scalability, cost reduction, or any number of objectives based on the business and system.
Select a Migration Plan and Strategy
The migration plan and strategy will include everything from project timelines and budgets for each phase to specific resources needed for completion. A successful migration relies on a detailed migration strategy. This can often be part of an application migration or a cloud migration strategy and will require making decisions about all aspects of the legacy system migration based on the different types of migration strategies and steps involved.
Set Up the Target Environment
The next step is to set up the target environment for the legacy system migration. This can vary in complexity depending on the chosen environment, such as a cloud or on-premises data center, which can both leverage virtualization and bare metal servers.
Choosing the right platform brings its own complexities that must be evaluated based on a host of factors surrounding business needs and the legacy system.
Execute the Migration
Migration execution will encompass data extraction, cleaning, conversion, and download to the new environment. Organizations may choose an all-at-once or incremental approach based on things such as duration and cost versus downtime and reduced risk of major disruptions.
Test the New System to Verify Migration Results
During system migration, the IT team must rigorously validate the new system throughout its setup and final stages. This will ensure data remains intact, encrypted, and well-organized, while vigilantly monitoring for corruption and system flaws. The goal is to confirm that all applications run smoothly and data interactions are error-free.
Train and Support Users
When the system is operational, it’s vital to equip users with detailed training on its use, particularly if there are notable functional shifts from the old to the new system.
Document, Hand Over, Monitor/Optimize, Review
The post-migration phase hinges on four pivotal phases:
- Documentation: Recording the current system’s features and dependencies
- Handover: Marking the transition of responsibilities and training for the new environment
- Monitoring and optimizing: Assessing and fine-tuning the new system for discrepancies and performance enhancements
- Final review: Conducting a retrospective evaluation to compare the new system’s performance and functionality against the legacy system’s benchmarks, integrating stakeholder feedback
Achieving a Seamless Legacy System Migration
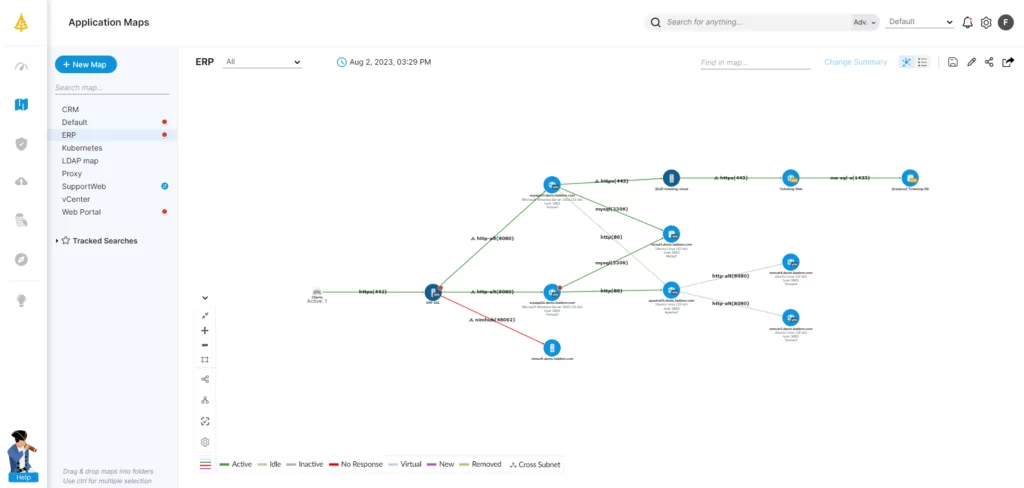
While every legacy system migration project is different, they all hinge on visibility at all stages of the process to ensure success. This is why comprehensive application dependency mapping and IT system mapping tools are critical to a seamless migration that balances continuity with innovation.
To learn how Faddom can support legacy system migration, read our complete guide to application mapping and fill out the form in the sidebar to start a free trial today!